As soon as most companies switched to remote work, people faced a lot of difficulties and cases of various cyberattacks.
The year 2020 showed us how important is to have a protected communication.

Illustration by Freepik Storyset
Our observation during the pandemic gave us a perfect understanding of how the lack of knowledge in cybersecurity can cause serious damage to the corporate environment.
After almost one year of working both remotely and in offices, the cybersecurity charts still display similar information — one of the most attacked targets are multiple industries, and the most popular attack techniques are malware:
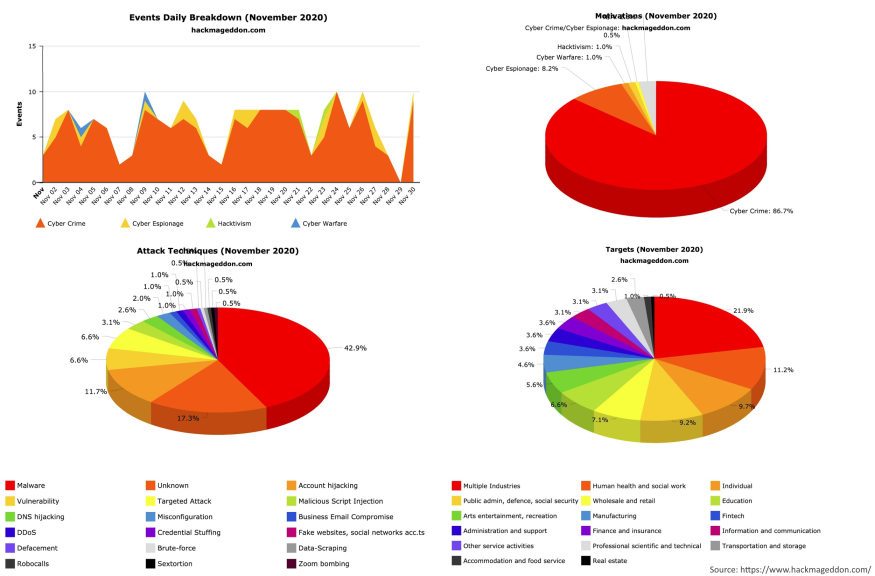
It means, that people still ignore the fact, that public services they using are not safe for sensitive information. Moreover, all cloud services became more vulnerable due to increased load. For example, on December 14, 2020, most of Google’s services were down for 45 minutes.
People continue to prefer convenience over privacy, and we want to warn you about possible threats in 2021.
Cybersecurity predictions and recommendations
- Malware. One of the most popular methods for invading user’s privacy would still be effective against people who download software from unreliable sources.
- Unstable cloud storage. The more people switch to remote work, the more load on cloud servers happens. One serious crash is enough to either create a security breach or cause a permanent data loss.
- Social media exposure. Be attentive when sharing personal information on social media as it can be used by hackers for invading your device or other illegal activities.
- Deepfake trending. Unfortunately, this amazing technology can be a potential threat for those who are not aware of it and can’t detect the difference between a scammer and a real person for some reason.
First, check the vendor’s reputation, and read reviews on trusted platforms (e.g. Sourceforge, G2, Capterra).
We recommend using your private servers that work in your local network.
Update your passwords regularly, use 2-step verification, or do not use social networks at all :)
For example, a person can send you a video asking for something (voice deepfakes are also possible to make). Tom Cruise's impersonator made a deepfake video about the actor, and it's absolutely mindblowing — it's very hard to tell the difference. This is not a fantasy movie plot anymore.
In general, always ask your security provider questions about services or software they offer to know how to manage the communication process properly.
| < <<<===== | =====>>> > |
|---|


